Although DDoS attacks declined slightly in 2018, the first quarter of 2019 saw an 84 percent increase over the previous year. The size and frequency of attacks surged, with the largest growth seen in attacks lasting over an hour.
Not only did these attacks double in quantity, but their average length also increased by 487 percent. As attackers increasingly utilize multiple attack vectors, cybersecurity experts turn to artificial intelligence and machine learning to identify patterns and bolster mitigation efforts.
What Is a DDoS Attack?
Distributed denial of service attacks aim to overload servers or disrupt network services by overwhelming them with access requests. These attacks can vary in method but often involve botnets.
What Is a Botnet?
A botnet is a virtual army of compromised computers and servers used to target a specific system. Hackers send malware to numerous systems, and if successfully installed, they can remotely control the compromised system’s processes to carry out the attack.
Types of DDoS Attacks
Volumetric Attacks
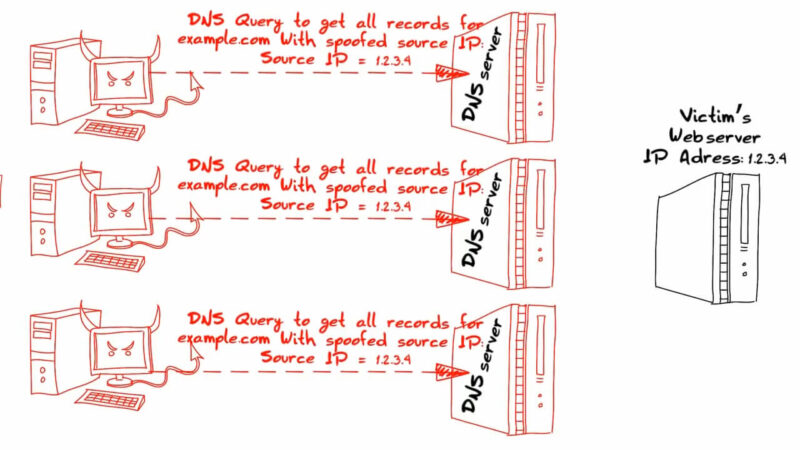
These attacks consume all available bandwidth on a network, preventing legitimate requests from being processed. A DNS amplification attack is a common example of a volumetric DDoS attack.
TCP Handshake/SYN Floods
Incomplete TCP Handshake protocol requests are sent to the target system, using spoofed IP addresses. This type of protocol attack can be exacerbated by legitimate site users refreshing their browsers, further contributing to the load.
Application Layer Attacks
Known as Layer 7 DDoS Attacks, these attacks send numerous HTTP requests to the server. Although low-impact for senders, they are resource-intensive for the server, which must load all the files and database queries needed for the website to display correctly.
Multi-Vector DDoS Attacks
Attackers may combine several DDoS attack methods to increase effectiveness and difficulty in countering. Targeting multiple network layers can significantly enhance disruption.
Challenges in Preventing DDoS Attacks
Preventing DDoS attacks is challenging due to their variety. Some attacks are difficult to distinguish from legitimate traffic requests, making mitigation efforts complex.
7 Biggest Recent DDoS Attacks
1. Amazon Web Services (AWS) (February 2020)
In February 2020, AWS mitigated the largest DDoS attack ever recorded, stopping a 2.3 Tbps attack. The attack, which utilized hijacked CLDAP web servers, caused three days of elevated threat for AWS Shield staff. CLDAP servers amplify DDoS traffic by 56 to 70 times its initial size, making them particularly problematic.
2. GitHub (February 2018)
GitHub faced a record-breaking 1.3 Tbps attack that flooded its servers with 126.9 million packets of data per second. The attack only took GitHub’s systems down for about 20 minutes due to a DDoS mitigation service that detected the attack and minimized its impact. This attack used memcaching, a strategy involving spoofed requests sent to vulnerable servers, which then flood the target with amplified traffic.
3. Undisclosed NETSCOUT Client (March 2018)
Shortly after the GitHub attack, NETSCOUT reported a 1.7 Tbps DDoS attack against one of their clients. Based on the same memcached reflection/amplification attack vector, the attack did not cause any reported outages, demonstrating the importance of preparedness.
4. Dyn (October 2016)
Dyn, a major DNS provider, faced a massive botnet attack using the Mirai malware, which incorporated IoT devices. The attack caused widespread disruption for Dyn’s customers, including Netflix, PayPal, Visa, Amazon, and The New York Times. The problems were resolved by the end of the day, but the attack highlighted the fragility of network infrastructure.
5. BBC (December 2015)
On the last day of 2015, a group called New World Hacking launched a 600 Gbps attack using its BangStresser application tool. The attack took the BBC’s sites, including its iPlayer on-demand service, down for about three hours. Notably, the tool utilized cloud computing resources from two Amazon AWS servers, a troubling development for IT security professionals.
6. Spamhaus (March 2013)
In 2013, Spamhaus, an industry-leading spam filtering organization, faced a 300 Gbps attack. The attack was launched by a teenage hacker hired by scammers. When Spamhaus turned to a DDoS mitigation service, the attacker shifted focus, causing network disruptions throughout Britain.
7. Bank of America/JP Morgan Chase/US Bancorp/Citigroup/PNC Bank (December 2012)
In 2012, a group called Izz ad-Din al-Qassam Cyber Fighters launched several DDoS attacks against US banks, disrupting services and causing severe slowdown. The attacks reached 63.3 Gbps at their peak, highlighting the need for robust cybersecurity measures.
The Role of Artificial Intelligence and Machine Learning in Mitigating DDoS Attacks
Artificial intelligence (AI) and machine learning (ML) are becoming crucial in identifying and mitigating DDoS attacks. These technologies can analyze vast amounts of data to detect patterns and predict potential attacks. By continuously learning from new data, AI and ML can improve their accuracy in identifying threats.
5 Steps to Safeguard Against DDoS Attacks
1. DDoS Mitigation Services
DDoS mitigation services offer specialized solutions to counter DDoS attacks. These services use various techniques to filter malicious traffic, allowing legitimate requests to reach the server.
2. Blended ISP Connectivity
Using multiple internet service providers (ISPs) can help distribute the traffic load, making it harder for a DDoS attack to take down the entire network. This approach ensures redundancy and enhances network resilience.
3. Regular Security Audits
Conducting regular security audits can help identify vulnerabilities in the network. Addressing these vulnerabilities proactively can reduce the risk of DDoS attacks.
4. Implementing Rate Limiting
Rate limiting controls the number of requests a server can handle over a specific period. This can prevent an overload of requests, helping to mitigate the impact of a DDoS attack.
5. Educating Employees
Educating employees about cybersecurity best practices can help prevent the installation of malware that could be used in a botnet. Awareness training can reduce the risk of systems being compromised.
Conclusion
DDoS attacks are a persistent threat to companies and their customers. While cybersecurity measures are improving, attackers continuously evolve their tactics. Understanding the nature of DDoS attacks and implementing robust mitigation strategies is crucial for safeguarding network operations.
By leveraging AI and ML, conducting regular security audits, and educating employees, companies can enhance their resilience against these disruptive attacks.
Related Posts:
- Which Industries Are Most At Risk For Cyber Attacks?
- What Are the Most Important Data Center Security Standards
- Horse Racing Laws: Most Important Rules to Protect…
- AI Beyond Robotics ─ The Most Unexpected Uses You…
- Are Bonus Buys Still the Most Played Feature in 2025…
- Why Do Most Apps Fail—and What Successful Teams Do…







